Protecting cloud resources is a top priority for every organization. To help with this, AWS comes with another security tool: AWS Inspector.
This vulnerability management tool automatically discovers your workloads and continuously scans for software and network vulnerabilities.
It supports EC2 instances, container images in ECR (Elastic Container Registry), and Lambda functions.
In this post, I will focus on scanning EC2 instances, generating reports, and exploring additional features.
My Lab Environment Setup
- EC2 Instance: RockyLinux 9.4 and AmazonLinux 2023 using t3a.micro instance type.
- AWS Inspector
By default, AWS Inspector is not enabled. You can follow the AWS Documentation 🔗 to enable it.
After activating AWS Inspector, the first step I took was to choose agent-based scanning for my EC2 resources.
AWS Inspector offers two scanning types: agent-based and agentless. To use both agentless and agent-based scanning, select “Hybrid” in the scan mode section of your account settings.
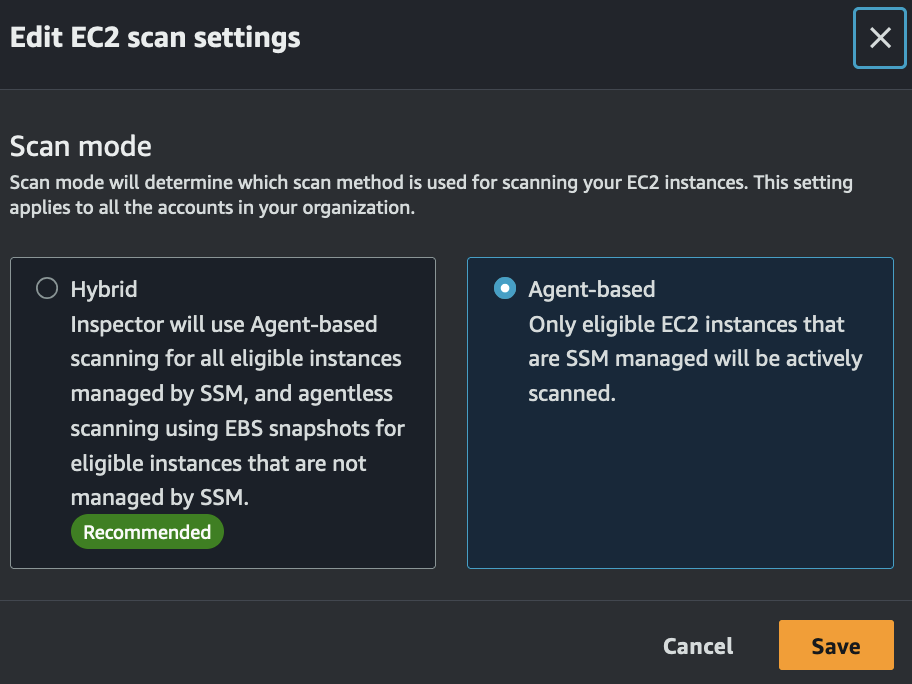
For agent-based scanning, it uses the SSM(Systems Manager) agent to scan resources. If your EC2 instance has the SSM agent installed, no further action is required; it will automatically install the Inspector plugin.
For agentless scanning, AWS first creates a snapshot of the EBS volume, scans it, generates findings, and then deletes the snapshot.
Scanning EC2 Instance
I created a EC2 Instance of Rocky Linux 9.4 image.
As soon as I configured SSM, my instances appeared in the AWS Inspector dashboard.
The scanning process took about 15 minutes, and once completed, the inventory was filled with vulnerabilities.
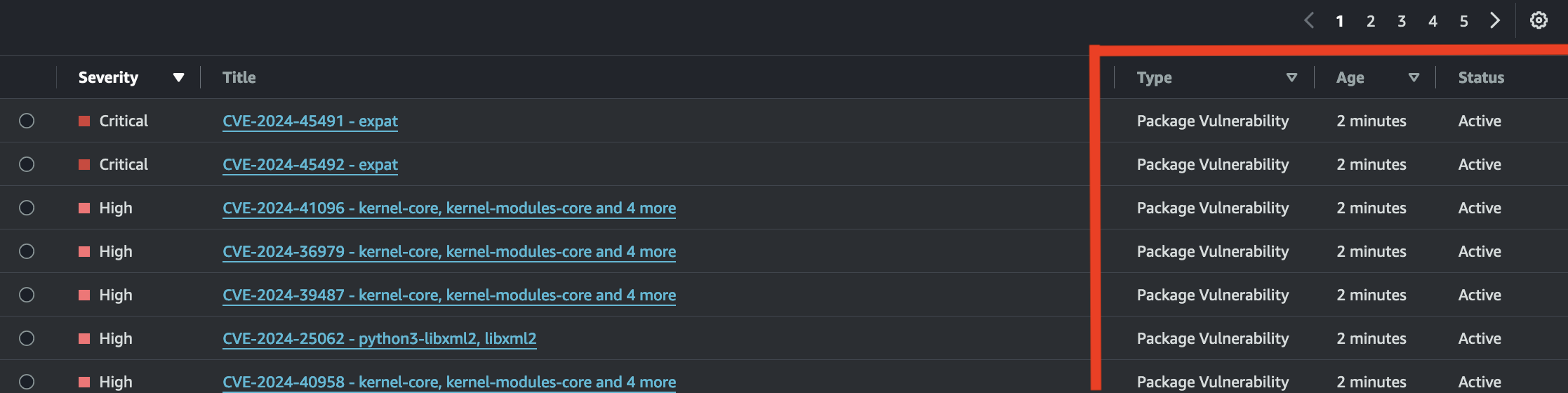
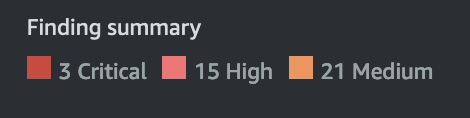
Before patching the server, I counted the total vulnerabilities. The result was:
Total: 39
Observing AWS Inspector Findings
AWS Inspector sources vulnerability data from the National Vulnerability Database (NVD) 🔗 .
It analyzes NVD data and scores, assessing EC2 Instnace’s criticality, such as network exposure, to provide a custom score.
For example, if the NVD assigns a risk score of 9 to a vulnerability, but your EC2 Instance is isolated and not exposed to the internet, AWS Inspector may assign a lower score for that vulnerability.
This is helpful because it allows organizations to focus on remediating the most critical issues first, reducing unnecessary panic.
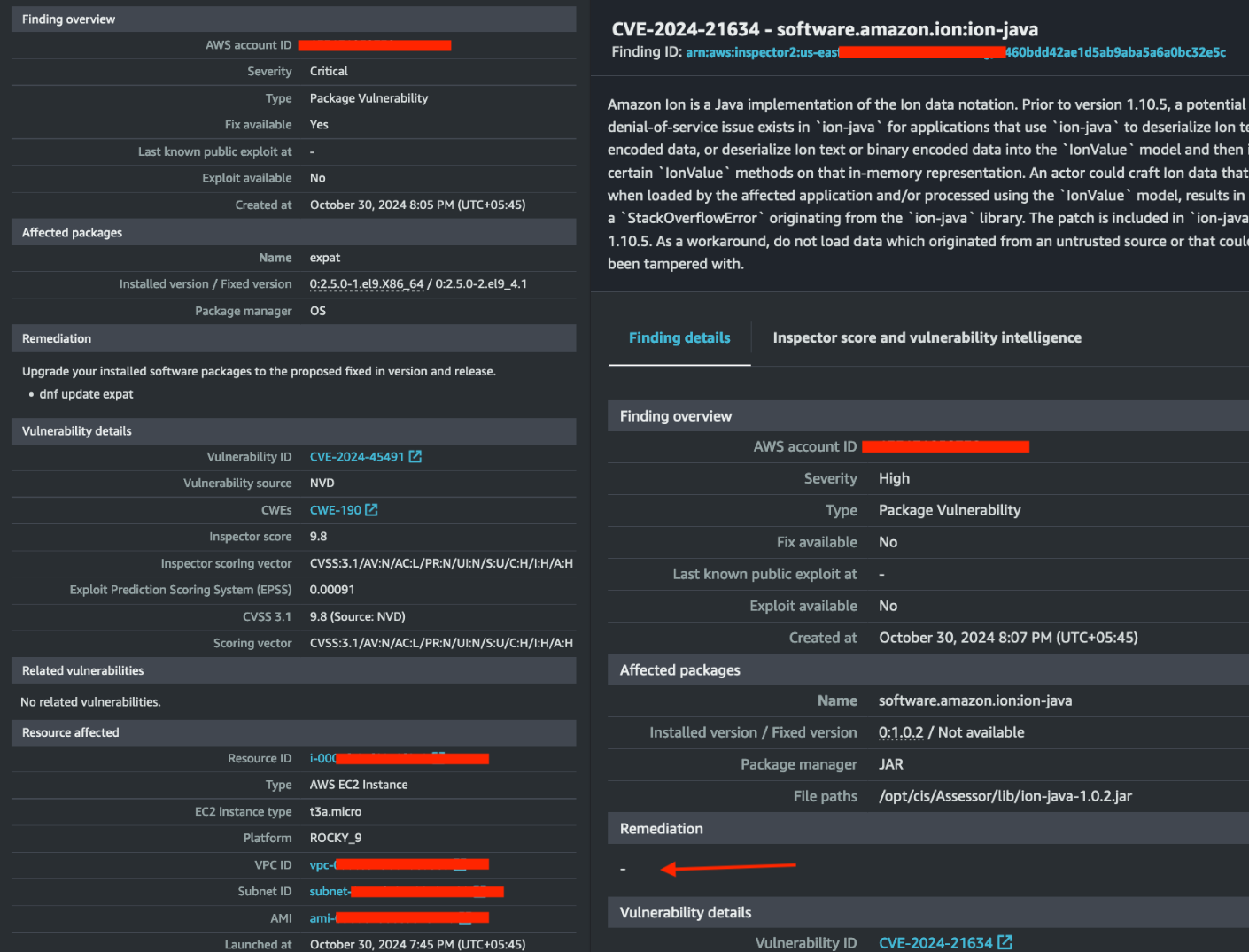
The vulnerability details were comprehensive, similar to those provided by other reputable third-party vendors. It included remediation commands to execute, along with the current and fixed versions, CVE IDs, score, instance details and more.
For some vulnerabilities, it didn’t provide specific remediation steps but offered a good summary with recommendations.
After that, I applied a patch to the server.
After patching and rebooting, I waited for the next scan to occur. The time interval for each scan of my EC2 Instance was 38 minutes.
AWS Inspector automatically initiates a scan when a new instance is launched, when new or existing packages are installed, or when new vulnerabilities are added to its database.
Although AWS Inspector scans continuously, I did not find an option to initiate on-demand scans.
I was impressed to see that the active vulnerabilities decreased to 9 after the patch.
AWS Inspector Deep Inspection
AWS Inspector also offers deep inspection for Linux EC2 instances. During this scan, it detects package vulnerabilities for supported application programming language 🔗 packages.
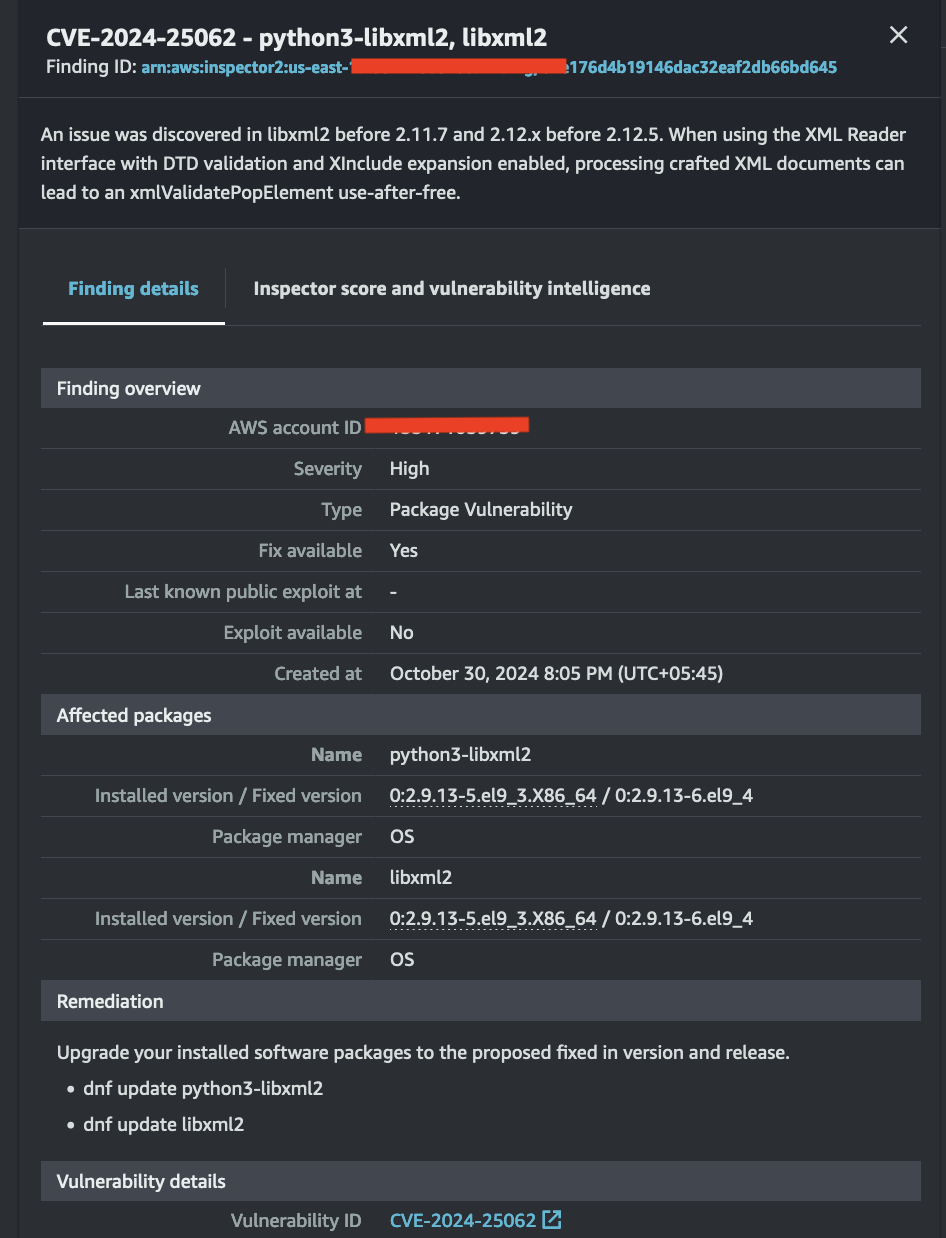
Below is the vulnerability detail for the Python 3 library found on my server, along with the remediation steps.
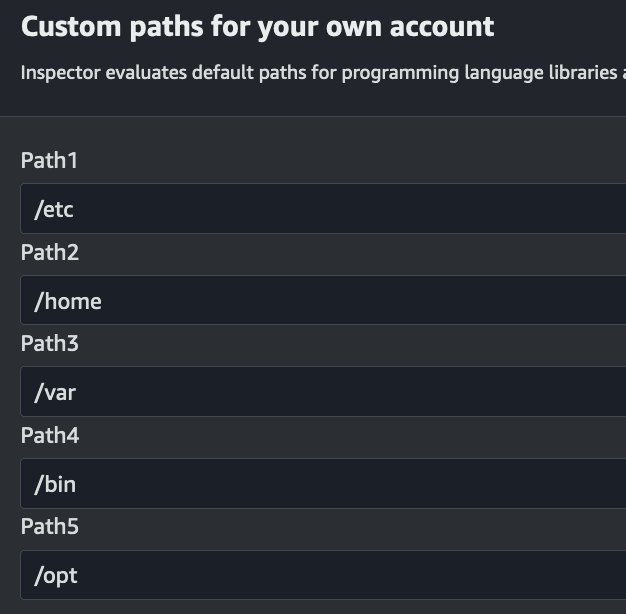
Another feature is the ability to add custom paths for scanning.
You can specify up to 5 custom paths, with each path required to be between 1 and 256 characters long.
This means you cannot insert paths like / or /var/www/html/projects/2024/client-portfolio/.
Monitoring Performance
I monitored the server while AWS Inspector was scanning to check performance and resource utilization.
I used a t3a.micro instance (1 GB memory and 2 vCPUs) and did not observe heavy resource consumption from Inspector.
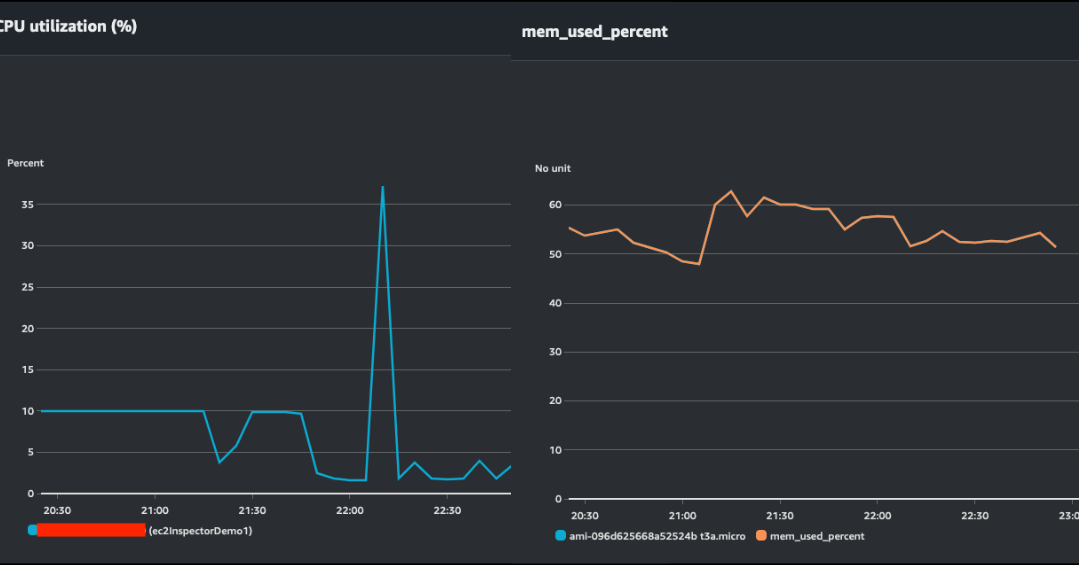
While memory usage appeared above average, it’s important to consider that the server was also running multiple different workloads.
Cost Consideration
AWS Inspector offers a 15-day free trial, after which you pay based on usage.
Charges are:
- For agent-based scanning, the cost is $1.2528 per instance.
- For agentless scanning, the cost is $1.7496 per instance.
AWS recommends using Hybrid scanning, but for cost optimization I prefer agent-based since it is cheaper.
With agentless, you incur additional costs for the snapshots AWS Inspector creates during the scan.
To further reduce costs, you can exclude unnecessary EC2 instances from scanning by implementing the InspectorEc2Exclusion tag.
Another great feature of AWS Inspector is the cost usage dashboard.
This provides monthly projected costs and the cost details for scanned resources across EC2 instances, ECR, and Lambda.
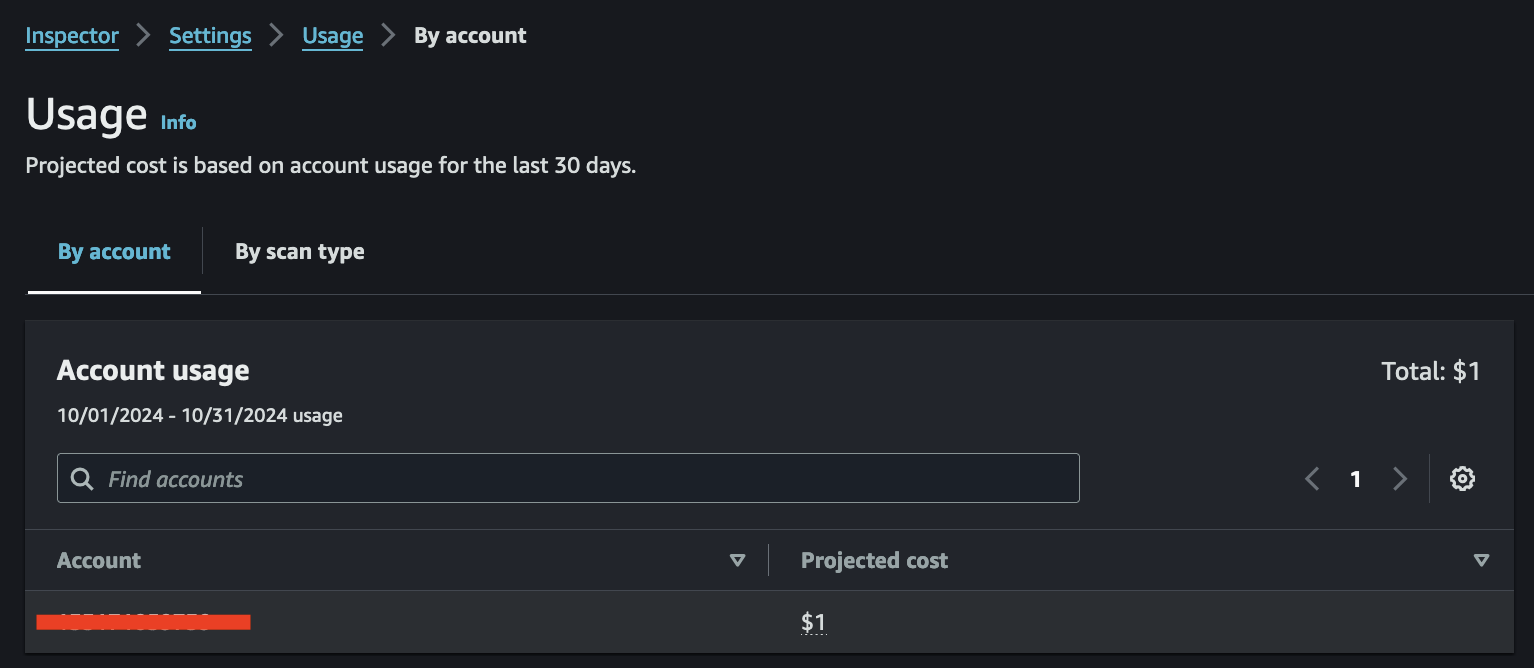
Additional Takeaway
AWS Inspector also allows you to scan for CIS benchmarks for your EC2 instances.
You can set up notifications or automation using AWS EventBridge for each new vulnerability detected.
This can be easily implemented across your entire AWS organization accounts.
Finally, I tried Amazon Inspector on a vanilla Amazon Linux 2023 and was surprised that it did not report any vulnerabilities.
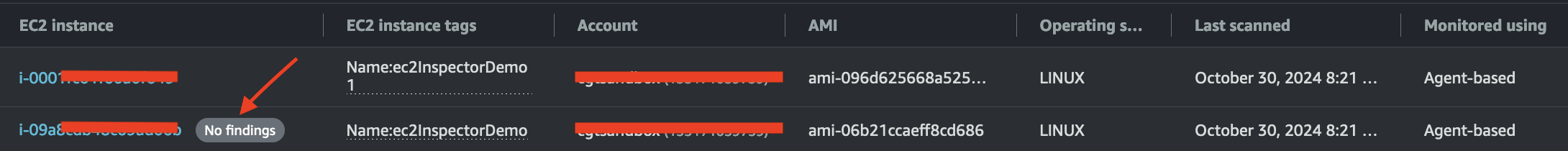
Does this mean that this image is completely free of vulnerabilities? 😁
Let me know your thoughts in the comment below.
Reference Link 🔗 .
Thanks for reading,
-Alon